Advanced digital technologies can generate substantial benefits, particularly in the form of enhanced efficiency and convenience across providing any service. Though we live in a digitally advanced world, major business processes still involve printing, scanning, and manual signatures. These paper-based processes not only create an unnecessary roadblock in the smooth functioning of workflow but also leave behind a destructive carbon footprint. A digital signature is a rescue to such situations. But does the law recognize a digital signature?
There are further questions that most people struggle to find answers to. How can you create a digital signature? What differentiates a digital signature from an electronic signature? Are these signatures secure? In this article, we’ll answer all your questions, and also explain what the law says on digital signature. But first of all, we need to explain some basic concepts.
What is a digital signature?
A digital signature, as the name suggests, is like a modern alternative to manual signatures on documents, engraved with paper and pen. They refer to a category of electronic signatures that use algorithms to generate a digital fingerprint also known as “Hash”. This hash value is unique to each document and will change if you make any changes to the document.
Also read: Hashing for dummies
Digital signatures ensure the authenticity and integrity of messages. The main role of a digital signature is to guarantee that no one is able to tamper with the contents of a message before it reaches its destination safely. To generate a digital signature, applications use an industry-standard technology called the public key infrastructure. This technology uses two-way cryptographic protection hence, making it more complex and nearly impossible to tamper with.
Also read: Asymmetric Encryption and Public Key Infrastructure
Digital signatures can appear on a document in the same way as signatures on a physical document and can include an image of a physical signature, date, location, and official seal. But, for some documents, the digital signature is not inherently visible. Nevertheless, it does not make the document invalid. The representation of signature varies from document to document and processing platforms. For example, an Adobe PDF that has been signed digitally depicts a seal icon and blue ribbon on the top of the document along with the signer’s name and the certificate issuer.
How do digital signatures work?
Let’s understand how this technology functions. Digital signatures use the public key infrastructure (PKI) and combine it with hashing. PKI uses two keys, a public key and a private key, that together create a key pair to encrypt and decrypt a message using a strong cryptography algorithm. Here’s how sending a digital signature works:
- A wants to sign a document X using his digital signature and send it to B. A selects the file and then his computer calculates the file’s unique hash value.
- Now, the computer encrypts this hash value with A’s private key to create the digital signature.
- A sends the file X, along with his digital signature, to B.
- B’s computer now uses A’s public key to decrypt the digital signature.
- Finally, B’s computer performs the most important function. It calculates the hash value of file X and compares it with the hash value it decrypted in step 4.
Phew! Seems like a lot of work? Not to worry, these minute processes are all taken care of by the computer/ software. No manual work at all.
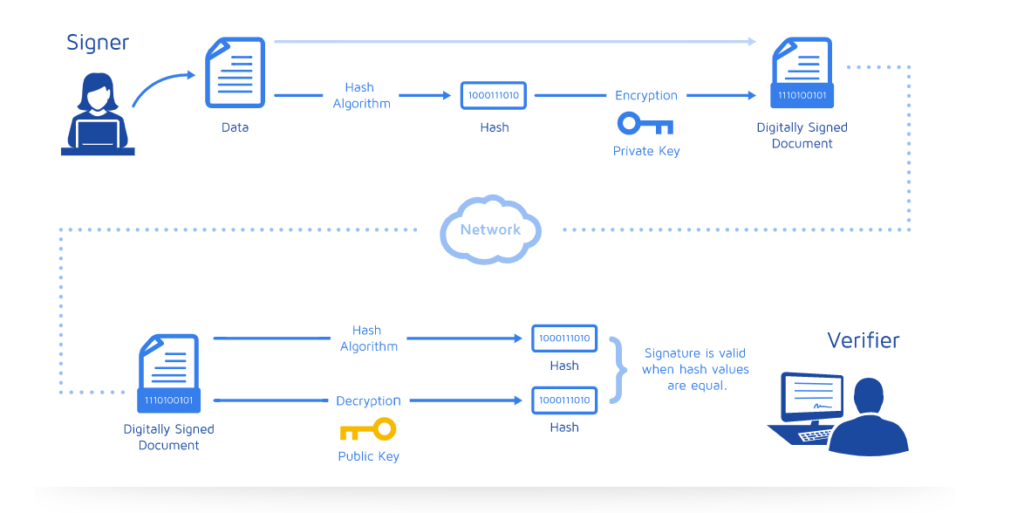
But what if the hash values don’t match?
Talking of the above example, what if B receives a file, performs step 5, but the hash values don’t match? Does this mean the data has been tampered with/ altered? Let us answer this question by understanding the process of verification of a digital signature.
Digital Signature is firmly based on proving that a digital message or document was not modified – intentionally or unintentionally – from the time it was signed. Digital Signatures fulfill that purpose by generating the hash value of the document. It is pertinent to recall here that the hash value of each file is unique. Any change, even minor, to the file will lead to the generation of a different hash value.
As a result, when the receiver’s computer compares the hash value as explained in step 5, any difference in the hash value means that the file has lost its integrity. Moreover, if the two hash values don’t match, there is also a possibility that the signature was created with a private key that does not correspond to the public key – simply an authentication issue.
Where can you buy a digital signature?
The techniques involved in securing digital records with digital signatures sure seem complicated, don’t they? How complicated would it be to create asymmetric keys?
Thankfully, you don’t need to perform any of the above steps, other than a few clicks. Multiple service providers create digital signatures. Usually, the service providers sign up with certifying authorities which issue digital signature certificates. All you need to do is sign up with a certifying authority like ‘eMudhra’ or ‘IDSign’ through service providers like ‘Adobe’ or ’emsigner.com’. Using e-KYC authentication, these service providers will give you a code that you can use to digitally sign any electronic record. For more on e-KYC authentication, you can read this article.
If the above process seems too simple, that’s because it is not complete yet.
Here’s why. Despite the digitalization of electronic records and digital signatures to authenticate them, risks of forgery still exist. As a result, the government closely regulates the use of digital signatures. In order to use a valid digital signature, you need a digital signature certificate. Who issues these certificates? There are certain ‘certifying authorities’ who receive a license from the government for this purpose. Supervising the certifying authorities, is the Controller of Certifying Authorities (CCA), appointed by the Central Government. [Section 17 of the IT Act, 2000]
So, how is it different from an electronic signature?
This confusion is more common than you’d think, given the very close meanings of the two words. Let’s find out how they differ. The three major bases for their difference are their scope, regulatory provisions and purpose. Electronic signatures cover a wider scope and can mean anything in the electronic form that indicates assent. This may include pictures, symbols, writing your name at the end of a document as well as digital signatures.
Also read: The law on Electronic Signatures
On the other hand, we can call digital signature the most secure kind of electronic signature (because of asymmetric encryption and hashing). This is also why digital signatures attract closer supervision and require technical standards, as compared to the other forms of electronic signatures. So how do you choose which kind of signature you want to use?
You may choose any form of an electronic signature to indicate assent to a particular electronic record. Whereas, digital signatures also verify the integrity of the contents of the electronic record. For many compliances, the government mandates the use of digital signatures. E.g. Registration of the director of a company.
The big question- What is the law on digital signature?
Section 3 of the Information Technology Act, 2000 empowers you to confirm the authenticity of electronic records by digital signatures. However, it is very technologically specific. It even defines all components of a digital signature and specifies how it should function.
Digital Signature: Section 3(2) says that authentication through digital signatures must use an “asymmetric crypto system” and “hash function”, which “envelop and transform the initial electronic record into another electronic record”.
Asymmetric Crypto System: Section 2(a) defines the asymmetric crypto system as a system of a “secure key pair” consisting of a “private key” for creating a digital signature and a “public key” to verify the digital signature.
Key Pair: As per Section 2(x), a key pair means a private key and its mathematically related public key, which are so related that the public key can verify a digital signature created by the private key.
Public Key: Section 2 (zd) defines the public key as the key of a key pair used to verify a digital signature and listed in the digital signature certificate.
Private key: As per Section 2(zc) it is the key of a key pair used to create a digital signature.
Hashing: Further, Section 3(2)(a) says hash function is an algorithm mapping or translation of one sequence of bits into another, generally smaller, set known as has result, such that an electronic record yields the same hash result every time the algorithm is executed with the same electronic record as its input making it computationally infeasible-
(a) to derive or reconstruct the original electronic record from the hash result produced by the algorithm;
(b) that two electronic records can produce the same hash result using the algorithm.
Other than these, Sections 17- 42 deal with the regulation of digital signatures.
Digital signature and the Law of Evidence
First of all, electronic records are admissible in a court of law by virtue of Section 3 of the Indian Evidence Act. However, if you’re a lawyer you must be wondering about the evidentiary value of an electronic record authenticated using digital signatures.
Section 67A
The fact that a Secure Electronic Signature belongs to the subscriber/ signer need not be proved in court.
In the case of secure electronic signatures (which only digital signatures are as per the Indian law at the moment), the control of the signature vests exclusively with the signatory. Further, it is the duty of the signatory to guard the private key. Why so? Simply because a certifying authority issues the private key (and the public key) and the authority can trace the owner of a signature.
Section 73A
The court can ascertain whether a digital signature belongs to the person who has affixed it: In order to do so, the courts may direct the signatory or the Controller of Certifying Authorities to produce the digital signature certificate.
The digital signature certificate contains the public key. The court may direct any person to apply the public key listed on the Digital Signature Certificate and see if it corresponds with the private key.
Section 85B
Presumption as to electronic records and electronic signatures: The Court shall presume that a ‘secure electronic record’ has not been altered until the contrary is proved.
What is a Secure Electronic Record?
Section 14 of the IT Act, 2000, says that when any security procedure has been applied to an electronic record, such record shall be deemed to be a secure electronic record.
Further, digital signatures are considered to be secure digital signatures if they fulfill the conditions given under Rule 4 of the Information Technology (Security Procedure) Rules, 2004. The advantage of a secure digital signature is, that the electronic record on which it is affixed, becomes a secure electronic record.
Hence, the court presumes documents signed using a secure digital signature to be authentic.
This article has been co-authored by Debdattaa Das and Rohit Ranjan Praveer.
Do subscribe to our Telegram groupfor more resources and discussions on tech-law. To receive weekly updates, don’t forget to subscribe to our Newsletter.