A few days back, a cybersecurity firm had claimed that the massive data breach at Air India was pulled off by Chinese government sponsored hackers. The cybersecurity firm Group-IB, through a blog post had related the Air India breach, SITA Passenger Service System, and the hacking group APT41. However, SITA has now issued a clarification to My Lawrd that the attack on SITA PSS and Air India hacking incidents were not linked or carried out by the same threat actor.
Attack on SITA PSS and Air India were not linked but separate
The Group-IB blog suggests that the attack on Air India’s network was the result of a sophisticated supply chain attack, which might have started with SITA.
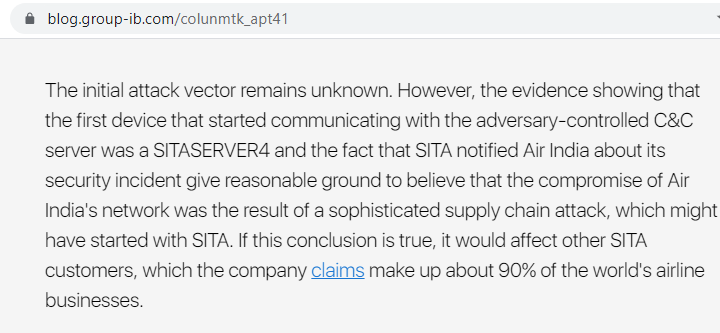
When Air India disclosed the breach, it said that its customers’ data was leaked due to a cybersecurity incident that SITA PSS suffered.
However, SITA has said that while Air India was impacted by the attack on SITA PSS, the alleged attack on Air India which Group-IB talks about in its blog was a separate, unrelated cyber-attack. Hence, there is no substance in the suggestion of Group-IB that the attack on SITA PSS and the separate attack on Air India were linked on carried out by the same threat actor.
SITA has further said that the Air India server named in the Group-IB blog was previously used to host in the Air India network some software provided by SITA to Air India. But this software was removed from the named server in 2019 and SITA is not aware if Air India is continuing to use the named server.
Based on its investigations, SITA adds that none of the methods that the blog suggests were used to attack Air India were employed in the attack on SITA PSS. The threat actor that attacked SITA PSS was expelled from its network several weeks before the blog suggests the separate attack on Air India began.
We will try to reach out to Air India with regard to this ‘separate incident’, and update the story once we get any information.
Do subscribe to our Telegram channel for more resources and discussions on tech-law. To receive weekly updates, don’t forget to subscribe to our Newsletter.