The CEO of Signal has hacked a Cellebrite phone unlocking system, pointing out vulnerabilities in Cellebrite devices that could be used against police investigators. Cellebrite is a digital forensics firm that creates tools and services for unlocking iPhones and other mobile devices. It is well-known for selling hacking software to governments and law enforcement agencies for investigation purposes, as well as to public school districts in the United States. Notably, the tool allows a user to circumvent encryption enabled messaging services such as Signal.
Interestingly, the Indian authorities have also expressed their interest in the tool. While the Hyderabad City Police is looking to acquire the tool, the Delhi police is already using it.
Vulnerabilities in Cellebrite
Moxie Marlinspike, the founder of Signal, reported many bugs in the hacking/ forensics hardware that could be exploited to run malicious codes on a computer used to analyze an unlocked system. In simple terms, it opens up the potential to allow an attacker to include a malware in any app, which when scanned by a Cellebrite device
As per him, Cellebrite has given little care to its own software security. He stated that there are “virtually no limits” on the type of malicious code that could be executed using the vulnerability. That could, in simple terms, means that the hacker gets hacked while playing out his tricks. That assumes all the more importance when the tool is used in a forensic laboratory.
For example, by including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures. This could even be done at random, and would seriously call the data integrity of Cellebrite’s reports into question.
The company also shared a video demonstrating the impact of a vulnerability. You can watch the video here.
Missing Updates
Pointing out the vulnerabilities, Moxie stated that industry-standard malware mitigation measures are inadequate. This creates “many possibilities” for exploitation.
The Cellebrite framework, for example, makes use of audio/video conversion software for Windows that was released in 2012. Since then, more than 100 security patches have been added to the app, none of which are included in the Cellebrite products.
A Possible Apple’s Copyright Violation
The company, for example, offers two software packages: UFED, which decrypts data to recover lost or secret data, and Physical Analyzer, which detects “trace events” for digital evidence collection.
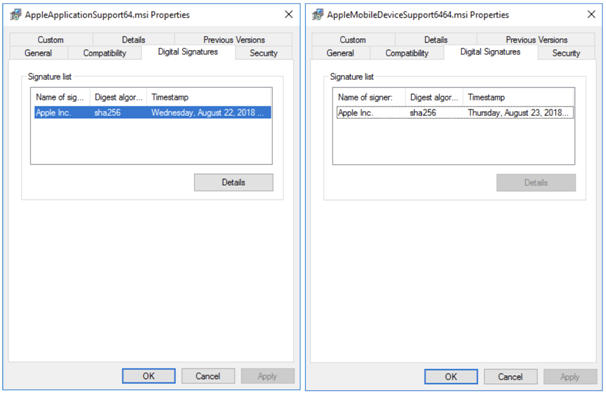
Moxie stated that while researching further, the Physical Analyzer (one of the devices of Cellebrite) supports MSI installer packages that have been digitally signed by Apple.
These bundles help to implement functionality that iTunes uses to interact with iOS devices. These features were allegedly extracted from the Windows installer for iTunes version 12.9.0.167. Moxie states that Apple is unlikely to have granted Cellebrite a license to use the programme, which means that its use may lead to legal issues in the future.
Do subscribe to our Telegram channel for more resources and discussions on technology law and news. To receive weekly updates, and a massive monthly roundup, don’t forget to subscribe to our Newsletter.
You can also follow us on Instagram, Facebook, LinkedIn, and Twitter for frequent updates and news flashes about #technologylaw.